Identification: Ethereum addresses serve as unique identifiers for each consumers and sensible contracts about the Ethereum community. They’re generated by way of the whole process of building an Ethereum account and therefore are accustomed to send and obtain money, along with communicate with sensible contracts.
Among the best tactics is to maintain your Ethereum addresses protected by making use of strong passwords and enabling two-variable authentication.
Hardhat is a improvement environment to compile, deploy, examination, and debug your Ethereum application. It helps developers when building good contracts and copyright regionally before deploying to your Reside chain.
I'm building a course on cryptocurrencies right here on freeCodeCamp News. The 1st section is a detailed description from the blockchain.
0x04345f1a86ebf24a6dbeff80f6a2a574d46efaa3ad3988de94aa68b695f09db9ddca37439f99548da0a1fe4acf4721a945a599a5d789c18a06b20349e803fdbbe
Continuing from our previous dialogue on distinguishing among differing kinds of Ethereum addresses, Allow’s now delve into Distinctive cases including deal addresses and multi-signature addresses, and discover their one of a kind qualities.
GitHub - danielewood/vanityssh-go: vanityssh-go helps you to generate ED25519 private keys with vanity general public keys
It really should return the PHP Variation; Otherwise installed, download the working system-precise PHP adhering to the instructions to the official PHP Web page’s download page.
A “vanity address�?is actually Click for Details a type of copyright address that conforms to specified parameters laid out by the creator, typically symbolizing their brand name or title.
In this in depth manual, we’ll check out the ins and outs of making Ethereum wallets. Now, you most likely by now know very well what an Ethereum wallet is, but do you understand how to build a person? In order to understand how to established one up, we’ve received you covered.
Even so, the python implementation allows you to see in depth the elliptic curve math utilized to derive the public crucial.
0x04345f1a86ebf24a6dbeff80f6a2a574d46efaa3ad3988de94aa68b695f09db9ddca37439f99548da0a1fe4acf4721a945a599a5d789c18a06b20349e803fdbbe3
But Profanity is one of the most well-liked tools as a result of its superior efficiency. Unfortunately, which could only imply that almost all of the Profanity wallets were secretly hacked.
Additionally, there are other profile filters to cater to your demands. These are definitely examples of typically applied wallets - you should do your very own exploration just before trusting any application.
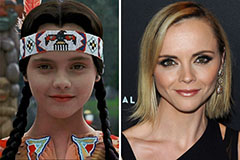 Christina Ricci Then & Now!
Christina Ricci Then & Now! Danny Pintauro Then & Now!
Danny Pintauro Then & Now! Jaclyn Smith Then & Now!
Jaclyn Smith Then & Now! Nicholle Tom Then & Now!
Nicholle Tom Then & Now! The Olsen Twins Then & Now!
The Olsen Twins Then & Now!